An introduction to cyber threat analysis for business leaders to keep their organizations safe from harm
Competing in today’s digital economy demands that businesses make cybersecurity a top priority. Keeping your data safe and preventing unauthorized access is not enough – you also need to stay ahead of the inevitable cyberattack.
Attacks come in the form of denial of service (DoS) attacks, viruses, malware, spyware, or merely because of a phishing email link that an employee unintentionally clicked. When ignored or not prevented, cyber threats result in service or business discontinuity, data loss, system or application unavailability, blackouts, military equipment or government system failure, and network disruption.
This is where cyber threat analysis comes in – an important cybersecurity strategy that helps businesses assess their security protocols, processes and procedures to identify threats, vulnerabilities and even gather knowledge of a potential attack before it happens. By understanding the importance of cyber threat analysis, business leaders can develop the essential cybersecurity strategies needed to keep their organizations safe from harm.
Cyber Threats are on the rise
The World Economic Forum reports that cyber attacks have been rated the fifth top rated risk in 2020 and will continue to as IoT cyber attacks alone are expected to double by 2025. The report adds that despite the dramatic and ongoing increase in incidents, the rate of detection is pitifully low at 0.05 percent in the U.S.
What is cyber threat analysis?
Cyber threat analysis is a system of tools, processes and people, for assessing, detecting and preventing the cyber activities and capabilities of unknown intelligence entities or criminals. Cyber threat analysis isn’t a one-time event – it’s an ongoing process that helps keep your business safe online! And the best way to prevent attacks is by being proactive – identifying and responding to developing threats before they escalate into bigger problems.
Why is cyber threat analysis important for businesses?
Cyber threats can impact businesses in a variety of ways, from damaging customer data to causing loss of revenue. Cyber threat analysis can help businesses identify opportunities for growth and improvement in their cybersecurity posture. By integrating cyber threat analysis into the overall cybersecurity strategy, businesses can better protect themselves from cyber attacks.
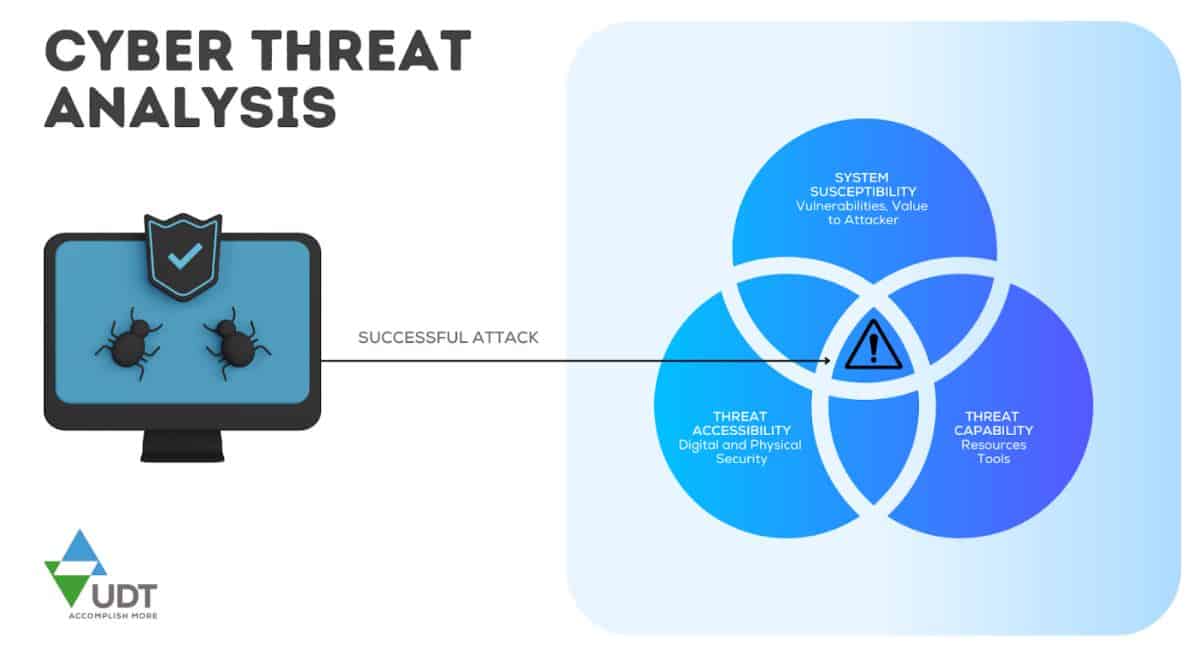
How does cyber threat analysis work?
(Components of the Cyber Threat Analysis Process)
- Scope
The first step in any cyber threat analysis should be to identify what will be included and excluded from the analysis. Included items are those items that should be protected from the threat. These are highly susceptible assets that could be accessed by malicious third parties. Then the level of sensitivity and the desired degree of protection of every item is drafted and extensively defined by analysts.
- Collection of Data
Assuming that the business meets all regulatory compliance standards with regard to data management, the first step is to collect information about the threat incidents. Examples could be phishing email header and content, uncovered hostile command and control infrastructure of IP addresses and domain names, URLs to malicious links, and so on. One must distinguish between real attacks from perceived threats in order to ensure that the focus is on the emerging threats that exist in reality.
In order to transform data into intelligence, an information technology analyst must be granted unrestricted system access. Research can be sourced from many places including internet searches, intrusion incidents, firewall logs, digital forensic analysis, reverse engineering of malware, digital forensic analysis, detection system logs, honeypots etc.
- Vulnerability Analysis of Acceptable Risks
At this stage, analysts check whether the security measures and policies are adequate protective measures. Penetration tests are also done to identify vulnerabilities and determine the extent of current exposure. The existing security defense is tested whether it has the capability to neutralize threats in terms of integrity, availability and confidentiality.
Threat analysis is a continuous process and not an occasional or a one-time event. It is an ongoing process that ensures that all safeguards are working properly. Risk evaluation should be incorporated in the overall life cycle. This helps in identifying risks that might have not yet reached their full blown stage, where they could cause maximum damage and loss.
- Mitigation and Anticipation
Finally, a highly qualified analyst will use the corpus of threat data identified to determine preventive measures. The analyst will categorize the threat data into groups, allocate each pattern to specific threat actors, and implement mitigation measures. Subsequently, the analyst must recommend mitigation strategies in anticipation of similar attacks in the future.
How to get started with cyber threat analysis
The growing sophistication of cyber criminals presents unprecedented business challenges in the area of cybersecurity. And organizations that do not perform threat and risk analysis are left open to attack which can lead to irreparable damage. Cyber threat analysis is an important first step to create a plan of action to protect your business.