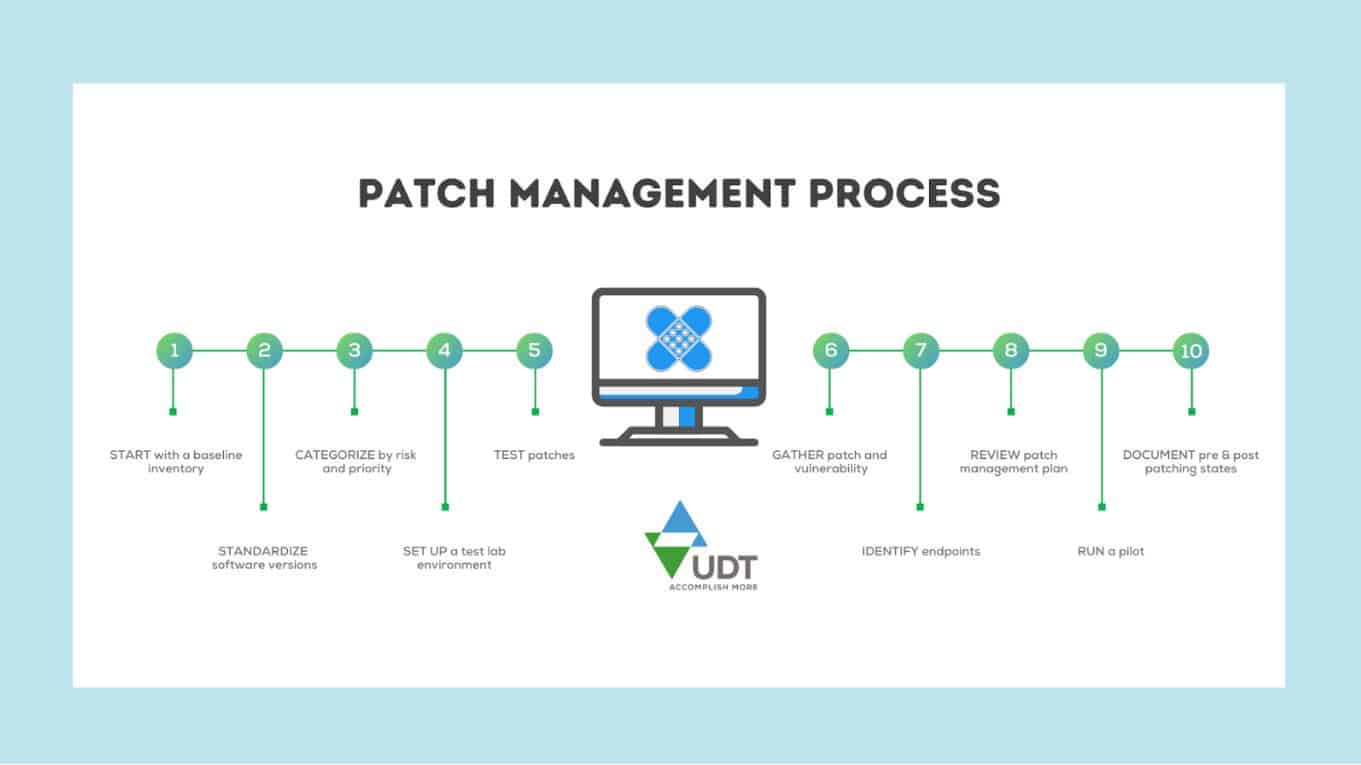
Why it’s crucial to have a Patch Management Process in place
You’ve often heard warnings about performing regular patch management but what does it mean?
Patching simply means keeping all your various digital assets (hardware, software, and network infrastructure) up to date with the most recent versions. However, Patch Management is easier said than done. As your business grows and day-to-day operations become complex, managing your interconnected systems can become unwieldy and unpredictable.
You will encounter problems such as — Which systems should you patch first? Your software stack or your vast network of distributed devices? Can you be proactive or automate patch management? Implementing a plan will not only provide answers to these questions but will also automate a process for regular and effective patching or system updates.
1. Failure to patch = attack
Recent incidents of data breaches have been mainly caused by unpatched systems. Hackers probe into your software, looking for unpatched systems to attack. 60% of organizations that experienced a data breach cited a known, unpatched vulnerability as the cause. Unpatched vulnerabilities refer to weaknesses that allow attackers to leverage a known security bug that has not been patched by running malicious code.
A report found that unpatched vulnerabilities are the primary drivers of ransomware attacks. It was recorded that in 2021, 65 new vulnerabilities arose that were connected to ransomware. This was observed to be a twenty-nine percent growth compared to the number of vulnerabilities in 2020.
Managing the patching process is somewhat different from vulnerability management. However, that latter is usually a much broader concept to manage all kinds of risks, not just the ones associated with outdated systems.
2. Regular Cyber Hygiene
Implementing regular cyber hygiene helps ensure that patching is consistently applied, tested and documented. Having a plan helps prevent common system failures like incompatible hardware issues with a patch, or a patch that installs well but breaks something else.
You want to have consistency across all of your Windows devices, for example, to ensure that you have found all the vulnerable systems, and that all patches have been successfully applied. This is where automated tools can come in handy. However, if your company does not have an IT administrator to get this done, finding the right managed service provider is the best way to stay on top of your patching needs.
3. Vulnerability Management
Vulnerability management is a much broader strategy of a patch management plan that includes discovering, prioritizing and resolving the security vulnerabilities of network assets. Patch management addresses the identified risks by upgrading software to the most recent version or by temporarily patching it to remove a vulnerability until the software vendor releases an upgrade that contains the fix.
A distinct category of tools known as vulnerability management software is used for scheduling and documenting these processes and partly automating them. Some vulnerability management tools have patch management as a component. Here are some vulnerability management best practices to add to your plan —
Network Scanning
Identify users and devices on the network (the same technique hackers use to search for vulnerable targets)
Penetration Testing
Mimics the tactics of hackers to identify vulnerable parts of the network
Verification
Confirms that a vulnerability identified during scanning and testing can, in fact, be exploited
Mitigation
Such as taking a vulnerable system offline, to prevent vulnerabilities from being exploited before a patch is available
Reporting
Uses data management, analytics and visualization tools for evaluating the organization’s vulnerability management process and complying with regulations.
Patch, Update and Protect
With UDT’s Lifecycle Management, you gain asset visibility to keep track of every EndPoint and guarantee they are always patched, updated, and optimally protected. With experience working with numerous industries in the private and public sector, along with our capabilities in IT security, we deliver an end-to-end service that ensures your security configurations are always compliant and up-to-speed.
Asset Visibility
Keeping EndPoints updated, patched, and protected can become an overwhelming exercise without proper asset visibility. We monitor and maintain every single EndPoint to ensure they are performing flawlessly, running all the latest updates, and properly secured against external and internal threats. Asset visibility will help minimize turnover, control support requests, and improve user experience.
Configuration Compliance
Your organization’s data holds sensitive information on your clients, partners, and employees. Because of this, industry standards and regulations have become stricter and more complex, making compliance a leading concern for many modern business leaders and IT managers. Through UDTEdge Secure Supply Chain and UDT Secure, We help you manage configuration compliance to ensure every EndPoint meets the necessary standard.