Technical Alert 032322001
Industries Affected:
- Financial Services
- Critical Manufacturing
- Government Facilities
Risk Rating: HIGH
SUMMARY
AvosLocker is a Ransomware as a Service (RaaS) affiliate-based group that has targeted victims across multiple critical infrastructure sectors in the United States including, but not limited to, the Financial Services, Critical Manufacturing, and Government Facilities sectors. AvosLocker indicators of compromise (IOCs) vary between indicators specific to AvosLocker malware and indicators specific to the individual affiliate responsible for the intrusion.
TECHNICAL DETAILS
AvosLocker ransomware encrypts files on a victim’s server and renames them with the “.avos” extension. AvosLocker actors then place ransom notes on the victim server and include a link to an AvosLocker .onion payment site. Payments in Monero are usually preferred but Bitcoin is accepted for a 10-25% premium.
Victims have been targeted in the United States, Syria, Saudi Arabia, Germany, Spain, Belgium, Turkey, the United Arab Emirates, the United Kingdom, Canada, China, and Taiwan. The leaked site includes samples of stolen victim data and threatens to sell the data to unspecified third parties, if a victim does not pay the ransom. AvosLocker ransomware is a multi-threaded Windows executable written in C++ that runs as a console application and shows a log of actions performed on victim systems.
INDICATORS OF COMPROMISE SPECIFIC TO AVOSLOCKER
Encryption and the ransom demand
Prior to encryption, the ransomware maps accessible drives and enumerated files in directories. It then encrypts files while creating a ransom note named “GET_YOUR_FILES_BACK.txt” in every directory.
Encrypted files have the file extension “.avos”, “.avos2”, or “AvosLinux”. Infected directories have a text file entitled “GET_YOUR_FILES_BACK.txt”. In some cases, the text from the text file reproduces on the desktop wallpaper of infected servers.
The “GET_YOUR_FILES_BACK.txt” file directs victims to an onion site accessible via a TOR browser, where the victim is prompted to enter an ID provided to them in the ransom note as follows:
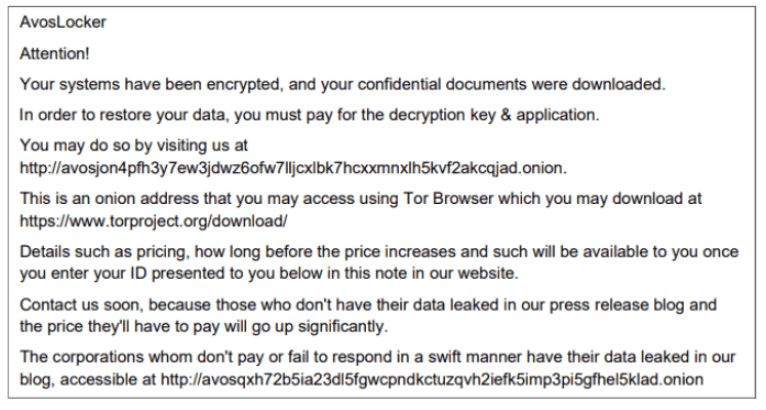
AvosLocker directs victims to in the “GET_YOUR_FILES_BACK.txt” file. The public site lists victims of AvosLocker, along with a sample of data allegedly stolen from the victim’s network. The leak site gives visitors an opportunity to view a sample of victim data and to purchase victim data.
Persistence mechanisms on victim systems include the modification of Windows Registry ‘Run’ keys and the use of scheduled tasks. Other tools associated with AvosLocker ransomware attacks:
- Cobalt Strike
- Encoded PowerShell scripts (publicly available tool)
- PuTTY Secure Copy client tool “pscp.exe”
- Rclone
- AnyDesk
- Scanner
- Advanced IP Scanner
- WinLister
VULNERABILITIES
Multiple victims have reported on premise Microsoft Exchange Server vulnerabilities as the likely intrusion vector. Other victims have mentioned specific vulnerabilities including the following:
- Proxy Shell vulnerabilities associated to CVE-2021-31207, CVE-2021-34523, and CVE-2021-34473, in addition to CVE-2021-26855. Intrusion vectors are likely dependent on the skillsets of the AvosLocker affiliate who infiltrated the victim’s network.
MITIGATIONS
- Implement or develop recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (i.e., hard drive, storage device, the cloud).
- Perform regular backups and specifically validate backup jobs which fail and understand why they’ve failed.
- Password protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Install and regularly update antivirus software on all hosts and enable real time detection.
- Install updates/patch operating systems, software, and firmware as soon as updates/patches are released.
- Review domain controllers, servers, workstations, and active directories for new or unrecognized user accounts.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind. Do not give all users administrative privileges. Disable admin accounts which have delegatable admin rights.
- Disable unused ports.
- Consider adding an email banner with the words “EXTERNAL EMAIL” to emails received from outside your organization.
- Disable hyperlinks in received emails.
- Use multifactor authentication where possible. For those accounts that cannot use MFA, implement strong password complexity policies with no less than 8 characters in length.
- Implement the shortest acceptable timeframe for password changes. Ensure passwords cannot be reused for multiple accounts.
- Require administrator credentials to install software and remove local admin privileges for users without the need for it.
- Avoid using public Wi-Fi networks. Instead, consider using a VPN with MFA.
- Conduct continuous security awareness and training exercises. Regularly provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).
RELATED UDTSECURE SERVICES
The following UDTSecure Cyber Security Services can help clients test and mitigate for this important vulnerability.
- UDTSecure AD Threat & Compromise Assessment
- UDTSecure Vulnerability Security Assessment and Patch Management as a Service
- UDTSecure Managed Threat Hunting Service
- UDTSecure Compromise Assessment