Organizations must be prepared to confront attacks on pace with the internet’s lightning speed, particularly Distributed Denial-Of-Service (DDoS) attacks, which are among the most significant threats they face. These attacks can be launched by botnets, networks of infected computers, often controlled by a single hacker or small team of hackers. They can overwhelm a network’s bandwidth, effectively causing a denial of service to all other incoming traffic and blocking access of legitimate traffic. Volumetric attacks, a type of DDoS threat, can flood the network with excessive traffic, overwhelming the system’s capacity and causing significant disruptions.
In the face of such threats, it’s crucial to look out for signs of a DDoS attack. This involves monitoring network activity and identifying unusual patterns that could indicate a DDoS attack. Network security measures, such as firewalls, intrusion detection systems, and similar protection services, can help in this regard by providing visibility into network traffic and alerting the organization about potential threats.
Data centers, which house an organization’s critical IT infrastructure, are often prime targets for these attacks. Therefore, securing these facilities is of utmost importance. This includes implementing robust authentication mechanisms to ensure that only authorized users can access the network resources.
The internet has become the backbone of any modern enterprise, regardless of the industry, location, or market to which they belong. Organizations must be prepared to prevent and mitigate the risk of DDoS attacks. This necessitates close collaboration with your Internet Service Provider (ISP), which can help monitor traffic patterns and identify unusual traffic spikes indicative of a DDoS attack.
One of the key defenses against DDoS attacks is authentication. By verifying the identities of all users trying to access the network, organizations can block malicious actors before they can launch an attack. This is especially important in preventing flood attacks, where the attacker tries to overwhelm the network with a deluge of requests.
Failing to endure a DDoS cyberattack and bounce back efficiently can result in a host of adverse outcomes, including loss of revenue, non-compliance, and reputational harm, among other things. As such, businesses must have a contingency plan for DDoS attacks. Like any business continuity plan, this strategy will evolve and must be repeatedly tested and refined over the years, if not decades. This plan should include a robust DDoS response protocol to ensure swift action against DDoS threats.
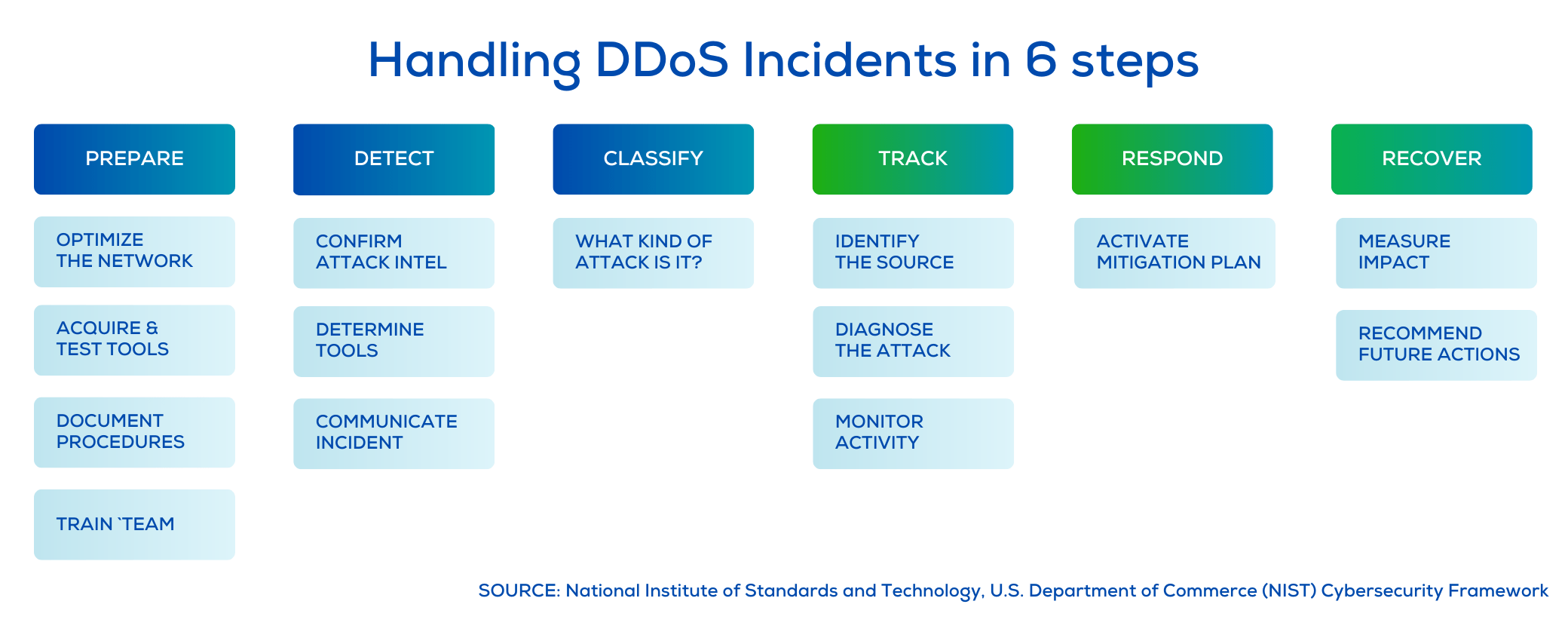
1. Get Prepared
The preparatory phase is the foundation for effective DDoS protection. It’s where you gather the tools, personnel, procedures, best practices, and communication strategies to tackle a DDoS attack head-on. It involves rigorous training, practice, and rehearsal of your plan to ensure that your organization can execute it successfully. The plan should encompass all aspects, processes, and procedures your organization requires to continue fulfilling its mission despite these attacks. This includes setting up firewalls and other DDoS protection measures to prevent malware from entering the network and forming botnets. A web application firewall can protect web servers from vulnerabilities that might be exploited by attackers. Regular patching of systems can also help to eliminate these vulnerabilities. Additionally, securing all endpoints can prevent attackers from gaining access to the network and launching amplification attacks, which increase the volume of traffic sent to the target. Lastly, consider implementing a rate limiting strategy to set a limit on the number of requests that can be made in a certain timeframe and blocks users, bots, or applications that appear to be flooding a web property with too much traffic.
2. Detect
With adequate visibility into internet traffic, organizations may be aware of DDoS attacks once they experience significant downtime lasting for days or weeks. Therefore, having the right tools to identify attacks and send timely alerts about abnormal and potentially hazardous events is crucial. Reliable attack detection forms the basis for the subsequent steps in the DDoS defense cycle. Cybersecurity tools can help to identify the IP addresses of bots involved in the attack.
3. Classify
Upon detecting an attack, the next step is to determine the type of attack and the specific target(s) involved. Accurately classifying the attack is crucial, as an incomplete or erroneous assessment could result in inappropriate and ineffective responses, potentially exacerbating the situation. This includes identifying the types of DDoS attacks, such as application-layer attacks, which target specific aspects of an application or service.
4. Track
Once the attack has been classified, the focus shifts to tracing its origins and determining the entry and exit points of the malicious traffic within your network. Automation should be leveraged for the detection, classification, and outlining steps to ensure that determinations are made swiftly and accurately, rather than relying on manual methods that are slower and more prone to errors.
5. Respond
Once you have identified and classified the DDoS attack, the focus shifts to mitigating the attack and ensuring the continuous availability of critical services. Selecting the appropriate mitigation approach is vital, and this decision should be based on the specific characteristics and scale of the attack. This could involve adjusting firewall settings, rerouting traffic, or increasing bandwidth to handle the additional load. DDoS mitigation techniques are essential at this stage to ensure that the network traffic is managed effectively, allowing legitimate users to continue accessing the services.
6. Recover
After the attack, conducting an in-depth analysis is vital. This postmortem analysis involves reviewing all actions taken during the attack, identifying areas for improvement, and using the lessons learned to enhance the overall DDoS defense plan. It will help to prepare your organization for future attacks better.
Forming the Incident Response Team
Determine whether a dedicated or contextual team is best suited for managing DDoS incidents. This team should include key stakeholders, infrastructure and service administrators, management, legal, communications/PR, and potentially external partners, suppliers, and customers.
Crafting the Incident Plan
A lack of planning will inevitably fail. Effective DDoS incident response hinges on the level of readiness and preparedness of your plan. Your response plan is the backbone for all six phases of DDoS handling. No plan is 100 percent perfect. It must be dynamic, adaptable, customized to your organization’s unique environment, and refined through regular practice and real-world scenarios.
Regular rehearsals are crucial This is necessary to ensure your plan is comprehensive and effective. These rehearsals should include internal-only drills and full-scale simulations involving all stakeholders, including external parties, to validate the plan’s readiness and identify any areas of improvement.
Achieving Cyber Resilience with UDT
Successful mitigation requires deliberate effort, not chance. This effort comes in the form of a comprehensive, well-tested plan executed as rehearsed. It is crucial to get your organization to work through each of the six steps, maintain internal and external communication throughout the incident, and conduct a thorough postmortem evaluation.
In the end, the goal is not just to survive a DDoS attack, but to emerge stronger and more resilient. A successful DDoS defense strategy is one that not only mitigates the immediate threat but also uses the experience to improve future responses and strengthen the organization’s overall security posture.
A continuous and automated approach is necessary to achieve such incremental improvements in cyber resilience without wasting time or resources. Leveraging systems to enhance the team’s capabilities can significantly extend cyber resilience. This includes the use of DDoS mitigation tools that can filter out malicious network traffic, ensuring that only legitimate users can access your services.
To find out how UDT can get your business or organization equipped with DDoS protection and other cybersecurity tools, contact us today to schedule an initial consultation.