
Whitepaper Courtsey of CISCO and Distributed by UDT
Imagine ordering a complete infrastructure and having it arrive in just a few days. Then provision that entire infrastructure, both physical and virtual, in minutes.
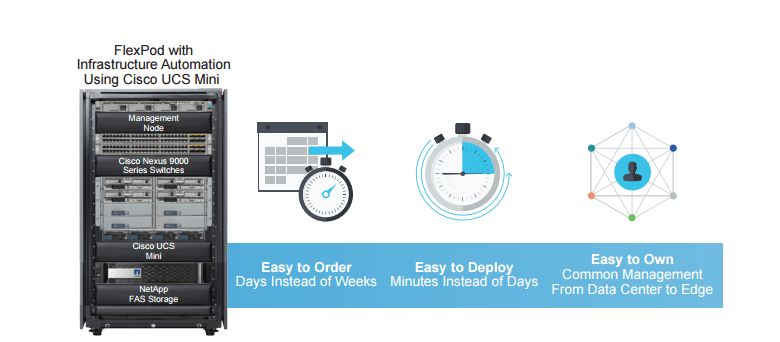
Imagine ordering a complete infrastructure and having it arrive in just a few days. Then provision that entire infrastructure, both physical and virtual, in minutes.