In 2021, losses from business email compromise (BEC) scams have exceeded those caused by ransomware. Here’s how you can prevent it.
Enterprise cybersecurity has been focused on fighting ransomware in recent years, but the latest FBI data suggests that BEC is the more pervasive threat. Businesses are losing 51 times more money from BEC attacks compared to ransomware.
In 2021, BEC attacks in the US caused total losses of $2.4 billion, a 39% increase from 2020. In contrast, at the same time, companies in the US lost only $49.2 million to ransomware.
FBI Internet Crime Report 2021
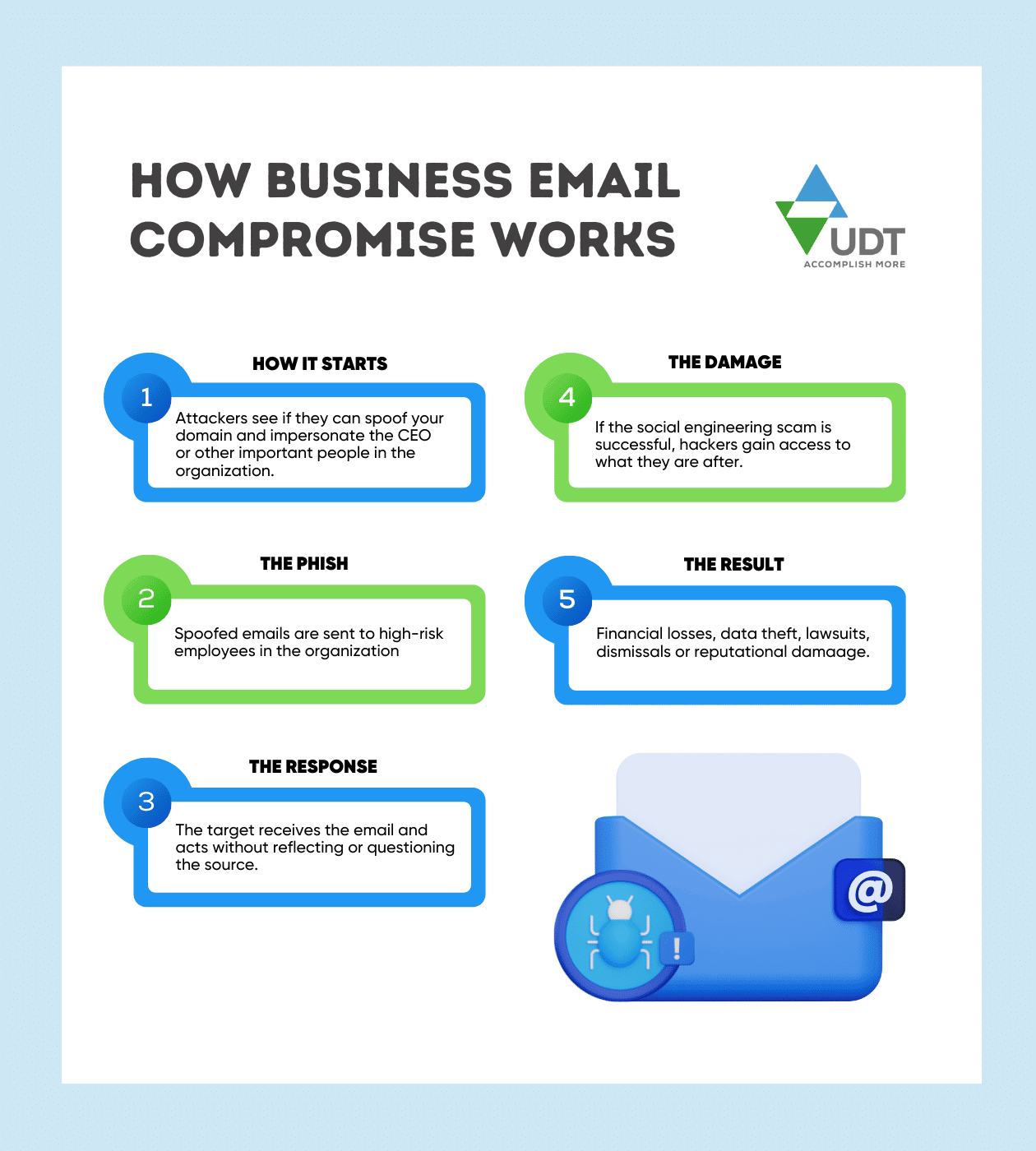
A typical BEC scam, according to the FBI, involves criminals sending an email message that appears to come from a known source making a legitimate request. All the messages were fake, of course. And in a successful BEC scam, thousands—or even hundreds of thousands—of dollars are sent to criminals instead, like in these examples:
A vendor your company regularly deals with sends an invoice with an updated mailing address.
A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
A homebuyer receives a message from his title company with instructions on how to wire his down payment.
Employ cybersecurity tools
To prevent BEC, Multi-factor Authentication (MFA) and spam filtering should be implemented across any organization dealing with digital transactions, as standard practices. Finding the best way to secure corporate data from hackers or other suspicious users can be a challenge for many IT professionals. Through Microsoft Enterprise Mobility + Security (EM+S), IT professionals can quickly install multi-factor authentication for enterprise accounts.
MFA involves users providing a cell phone number or back up email, which bolsters security by asking for additional pieces of evidence. These generic codes are sent directly to the user, and act as a supplemental shield to traditional passwords.
Once those are implemented, the next step is to further reduce your organization’s attack surface with next-level security layers. For example, using conditional access to use email only from specific geographic locations and devices.
Intensify security awareness training
Along with cybersecurity tools, organizations can institute ongoing employee security awareness training to reduce instances of BEC. Security awareness training programs should also highlight the importance of following up on suspicious activities.
If a person suddenly changes their account or how they are paid, that should raise a red flag. Additionally, any change should be followed up by an immediate phone call to confirm. This helps to verify identity and flag fraudulent emails before an incident escalates.
Preventing and mitigating BEC requires the involvement of everyone in the organization. By focusing on employee cybersecurity training, implementing standard security measures in the organizational network, and responding quickly to a breach, security professionals can reduce their risk of BEC.
Employees are the “tip of the spear” when it comes to cybersecurity and defense. If your employees receive regular security awareness training, their calculated decision-making and quick response can effectively block BEC, rather than entirely depending on your IT team.
Responding to a BEC attack
Even with all the security training, policies and technology tools in place, at some point in time, someone will eventually make a mistake. In any case, organizations must always be prepared to act in the aftermath of a breach. Here are some actions to mitigate the impact of a successful BEC attack.
- Change all user passwords
- Review the rules dealing with forwarding to outside accounts
- Review any logs to determine which data and accounts were compromised
- Assume all information in the mailbox is compromised, in case logs are not detailed enough
- Contact affected individuals that may have their data leaked
- Refer to this guide on how to communicate data breaches to customers
- Finally, draft a detailed review on how the BEC incident happened for employee training education and reference
Integrate security policies with business processes
Embedding data security policies right into business processes help organizations stay protected against such scams. For example, the process for updating payment details of a supplier must first comply with the company’s security policies. And the same steps should be applied consistently when signing a new vendor.
Experts also suggest enforcing a simple, standardized way for staff to report things that don’t add up. For example, if there’s an email that’s not monitored directly by the SecOps team, create one right away. If you think someone’s account might have been hacked, remind staff not to use that same account to voice your suspicions, whether it’s an email address, a Facebook account or a phone number.
A tiny dose of suspicion goes a long way
If you notice anything unusual, if anything is unexpected, check and confirm before making any payments. Validate the request with a quick phone call before going ahead with any official financial transaction.